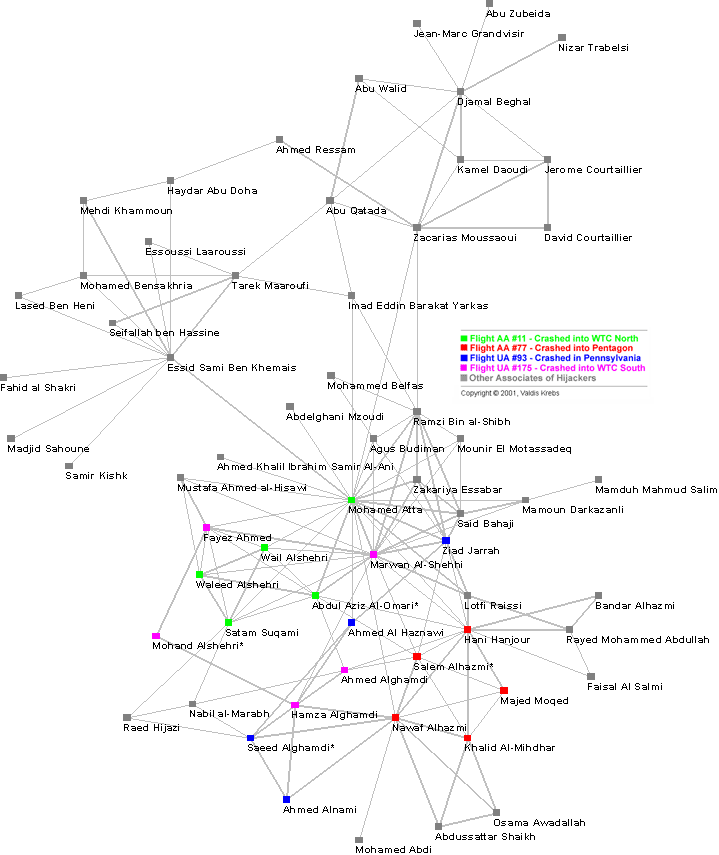
As we have begun discussing in lecture, networks can be viewed as the positive and negative relations between various individuals or groups. What happens when everyone in a network teams up against another group and forms a mass plan of destruction? You get a network of terrorists. The most studied terrorist network is that of 9/11, where there were nineteen hijackers who were all somehow connected to one another and who all had the same goal of mass homicide. Valdis E. Krebs worked on deciphering this intricate network and describes his findings in “Uncloaking Terrorist Networks”. Within this journal, Krebs expresses the significant role that this network played in finalizing the highly structured plan of the plane crashes. However, when attempting to uncover a terrorist network, numerous problems arise including: the lack of completeness (there are often missing nodes which investigators will never uncover), ambiguous borders (who is or is not considered part of the network), and the constant movement and revolution within these networks. Nevertheless, Krebs was able to construct a fairly detailed representation of the network. His discoveries were quite astonishing. Within the network, the average distance between two hijackers was 4.75 (which is rather high). However, certain shortcuts and secret meetings which occurred in Las Vegas before the attacks decreased this length to 2.79. This information relays an important aspect of terrorist networks. Commonly, these networks have a spaced out operational network, a larger administrative network, and distinct leaders. By having a more spread out network, Bin Laden ensured a sense of security inside the network. In order to make sure that the plans got carried out despite these sparse connections, there was an administrative network creating shorter paths between the hijackers. The hijackers trusted each other because they all had past relationships from their training camp in Afghanistan (however, these past associations remained rather suppressed, ensuring that the network stayed dormant).This sense of trust and administration enabled the terrorists’ plans to be successful.
As these networks develop, a primary leader typically arises. In this case, Mohammed Atta (note the green square in the center of the image) arose as the leader, having twenty-two connections to other nodes. Atta became the gatekeeper or bridge, controlling where and to whom information traveled. His central position and proximity to others gave him access to outside information. This enforces the notion of the ‘strength of weak ties,’ where the most valuable information can be exchanged by people from otherwise unconnected social networks. Atta was provided with this tremendous power, but even if he was removed from the network, there were numerous other people with connections who would be able new to arise as new leaders. This is quite significant in a terrorist network; in order to disturb the entire network, multiple highly connected targets must be simultaneously eliminated before new leaders arise. This provides terrorist networks with the strong ability to resist attacks.
Thus, it is clear that there are numerous facets contributing to a clandestine network. While in typical networks, strong ties are quite prominent, in a terrorist network, the strong ties are rarely activated, and therefore, appear rather weak. This enables the network to remain hidden and difficult to detect. The hijackers made few connections outside their network, maintaining the secrecy of the group. While one cluster did center around the pilots, and therefore, it became more susceptible to disruption, the overall network was rather successful in creating discrete ties with numerous layers in order to ensure that the final plan would be able to be completed.
Below is an image of the network created by Valdis Krebs (notice the more dense network around the pilots):
For more information on terrorist networks, one can read the New York Times Magazine article entitled, “Can Network Theory Thwart Terrorists” or visit John Robb’s (author of Brave New War) weblog on “The Optimal Size of a Terrorist Network.”


[…] and Combating Terrorism: jerseygirl15 points out the networked nature of terrorist cells. One might also argue that analyzing network structure (say within the telecommunications network […]
[…] and Combating Terrorism: jerseygirl15 points out the networked nature of terrorist cells. One might also argue that analyzing network structure (say within the telecommunications network […]