Lately in class, we have been discussing the evolution of information networks. With the creation of these networks, we have all benefited from rapid search, aggregation of data from diverse sources, and presentation of data based on ratings of relevance. With such speedy access and facilitation of information flow, how could these information networks ever create a disservice to individuals such as you and me? Well, consider a concept addressed in the earlier part of our classes as well as a fairly recent post: structural holes. As posited by Burt, the benefit of spanning a structural hole was the “gatekeeping” role, the ability to restrict the flow of information from one component to the next. Now consider how such “gatekeeping” could exist in an information network. With the rapid aggregation of sources and the more permanent structure of information in the digital context, the individual web user has very little control over the flow of information throughout the network. The main question that arises is: are all forms of structural holes obliterated with the creation of the internet? The working research by Danah Boyd, Jeff Potter, and Fernanda Viegas shows that though the internet has weakened an individual’s ability to maintain structural holes, we have created unique identity preservation methods to maintain structural holes in the social context.
Burt specifically speaks about the benefits of structural holes in the industrial, organizational context. As further discussed in class, those who span structural holes have the 3 following advantages:
1)Informational: early access to non interacting parts of the network
2)Creativity amplifier: those bridging structural holes can create novel solutions by combining information from various sources
3) Gate keeping: those who span structural holes can decide if nodes in one component can receive information from nodes to another component.
So in the business context, it appears that those spanning structural holes benefit from their controlling position. However, a Bearman-Moody study found that structural holes in the social context may be detrimental. With very little embededness and congeniality among friends, those spanning structural holes are exposed to variety of norms. Such a lack of a tightly-knit social support system could cause undue stress on the individual. Though the Bearman-Moody study confirms the notion that structural holes may be detrimental in the social context, there are many ways that we create beneficial structural holes in the formation of our identity. Boyd, Potter, and Viegas discuss the role of structural holes in social identity formation. The authors proffer that we have two sets of identities that interact and help form the other. However, the basis for each identity is distinct. First, we have a personal identity, formed from our innermost thoughts and values. Second, we have a social identity that we form from the various network contexts we are in. For example, the person I portray to a group of friends is very different from the person I portray to my family, professors, or coworkers. It is such a bifurcation of self where structural holes play an integral part in maintaining harmony among our many social identities. For example, it would be very troublesome (to me at least) if I ran into the interviewer for a summer internship while I was in a less decorous state at a local hotspot.
So even though structural holes may be detrimental by exposing us to a variety of norms that we may find hard to balance, they offer benefits by allowing us to maintain various social identities. Maintaining such separation is relatively easy in the physical world. There are many mechanisms to maintain structural holes such as physical separation or temporal separation. Furthermore, there is a mutability aspect of information shared with those in physical networks. The ability for information to pass from one component to the other depends on the level of separation of the components as well as the particular nodes even remembering the shared personal information. However, in the digital context, geographical separation is not a factor and there is a level of immutability of information shared. With the millions of archives that can be accessed through just one link, fortuitous “forgetting” by nodes is not as prevalent among a digital network. Furthermore, multiple corporations have devised methods of detecting exactly who we are through cookies and emerging software to identify individuals by patterns of speech. Though it may appear that maintaining control over a distinct and private identity is impossible in the digital network, the authors’ intensive review of a 5 year email record of “Mike” proves that we have created clever means to maintain a distinct identity among our social cohorts.
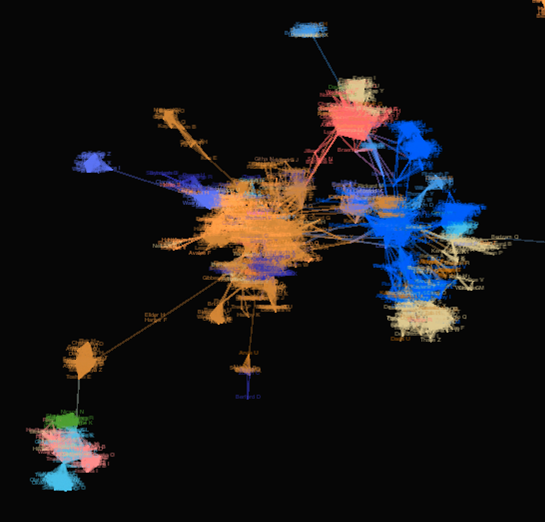
figure 1: example of “Mike’s” structural holes in email accounts
The first simple method of maintaining structural holes in the information age is to send different messages to different groups under a different email alias. For example, let’s say I want to invite my family, friends, and possible employers to a mixer I am having. I will first write three distinct messages: one with a sentimental and loving tone for family, one with a naughty tone for friends, and one with a formal tone to possible employers. However, a possible problem is that my brother might interact with my friend in a chatroom. He might notice my email alias on her list of friends and somehow gains access to my naughty message. In this case, the bridging mechanism of the internet has beaten my attempts to maintain structural holes and has created a bridge, eliminating my control over my bifurcated personality. I might combat this phenomenon by creating multiple email aliases for each component.
In their paper, the authors propose that we maintain structural holes by our email strategies. In terms of game theory, it is our dominant strategy to maintain a different self for every network and context. No matter what other nodes do, our ability to adapt to situations will expose us to a variety of networks thus conferring informational and social advantages. The gist of the author’s argument is that we establish trust and maintain our different personas through email functions such as the carbon copy and blind carbon copy. The three ties according to the article are knowledge ties, awareness ties and trusted ties defined as follows:
Knowledge ties: If A sends a message to B, then we assume that A knows B but not necessarily that B knows A. (This is a good example of the directional edges seen in many link connections in informational networks)
Awareness ties: If B receives a message from A, then B is “aware” of A. Furthermore, if B and C receive a message from A then B and C are aware of each other. In this example, B and C would most likely be two nodes from the same component. It would not be detrimental to A if B and C somehow contacted each other without A present
Trust ties: If A sends and message to B and Blind Carbon Copies the message to C, then we assume that A “knows” and “trusts” C. This assumption makes sense because C has the ability to respond and reveal to B that A sent a message to others without his awareness.
The working paper goes through an example of Mike’s email to a group of friends to illustrate the difference between knowledge, awareness, and trust ties. However, the main take-away message from the paper is that even though digital contexts have limited our ability to maintain structural holes, we have found methods to subvert complete access to ourselves and have been able to maintain many social selves.
Figure 2: Mike’s many different social selves Blue: friends Brown: School Pink: work Green: Website, images retrieved from powerpoint presentation link to presentation:http://smg.media.mit.edu/projects/SocialNetworkFragments/presentation/sunbelt.ppt
The article and accompanying slide presentation on the site offer a unique integration of concepts addressed at different periods of our instruction. We see how the digital world has hindered our ability to maintain structural holes, but that we have created novel methods to adjust to such restraints. This work illustrates one of the key concepts of network analysis: a network is the sum of our interactions which we in turn react to.
An interesting topic that the article addressed that is similar to concepts in class, but not directly discussed in class was that of “Simmelian ties” proposed by Krackhardt. According to Krackhardt, and individual is Simmelian tied to another if 1) they share a strong tie with one another and 2) if they share a strong tie with at least one other person. Such a concept brings strong triadic closure to a whole other level. Now, rather than the formulation of a weak or strong tie, under Simmelian ties, a clique must consist of at least a triangle with all strong ties.
Simmelian ties and “Mike’s” digital identity formation are more exhaustively described by
Danah Boyd, Jeff Potter and Fernanda Viegas in their working paper:
Fragmentation of identity through structural holes in email contacts.
Link to Site http://smg.media.mit.edu/projects/SocialNetworkFragments/presentation/index.html
Link to paper:http://smg.media.mit.edu/projects/SocialNetworkFragments/presentation/HalfPaper.pdf



* You can follow any responses to this entry through the RSS 2.0 feed.